Questa è una vecchia versione del documento!
Indice
Passi per configurare Shibboleth service provider su Windows Server + IIS
- Sistema operativo: Windows Server 2016
- Versione IIS: 10.0.14393.0
- Versione shibboleth SP: 3.0.4.2
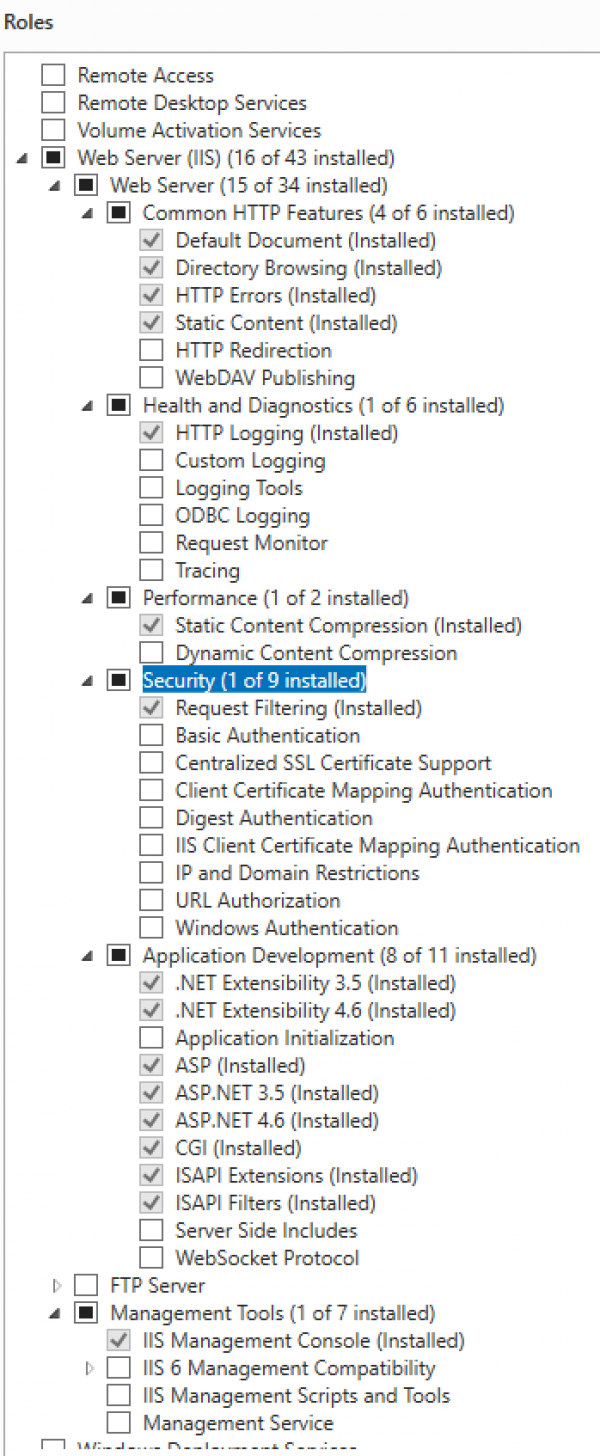
Ruoli e funzioni Windows Server
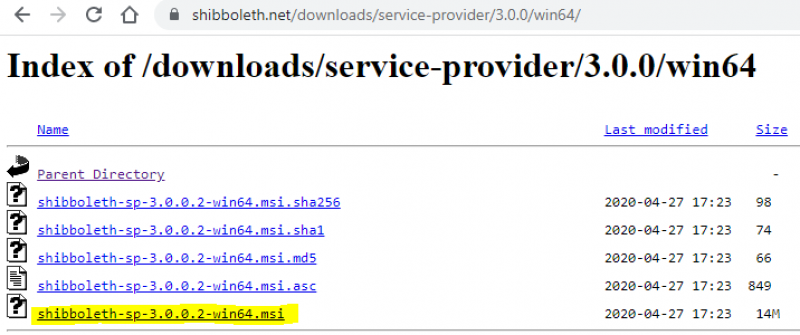
Download Shibboleth service provider
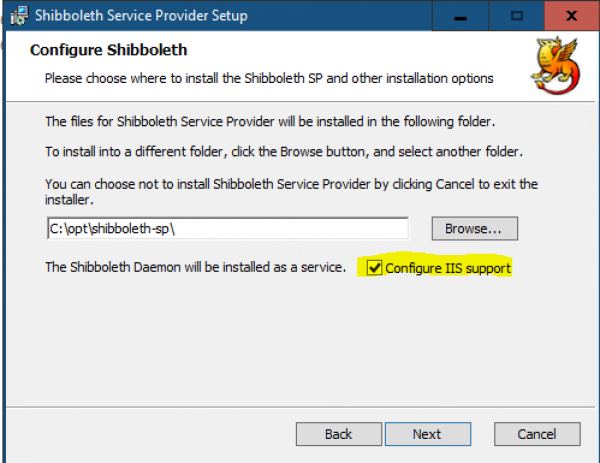
Installazione Shibboleth service provider
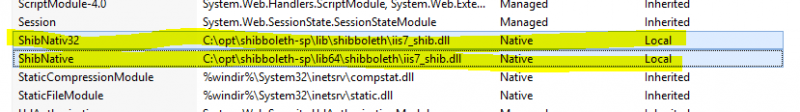
Verificare la corretta installazione delle DLL in IIS
Verificare che nel Site opportuno, nella sezione “Modules” abbia le i moduli nativi Shibboleth (32/64 bit)
Configurazione shibboleth service provider
(cambiare cartella in C:\opt\shibboleth-sp\etc\shibboleth)
shibboleth2.xml
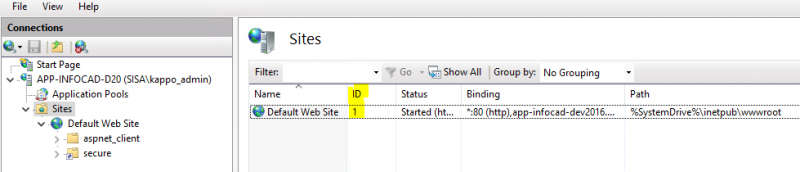
(Sezioni da personalizzare) Site id deve corrpispondere all'ID presente in IIS; il Site name corrisponde all'host (FQDN)
<ISAPI normalizeRequest="true" safeHeaderNames="true">
<!--
Maps IIS Instance ID values to the host scheme/name/port. The name is
required so that the proper <Host> in the request map above is found without
having to cover every possible DNS/IP combination the user might enter.
-->
<Site id="1" name="app-infocad-dev2016.unipr.it"/>
<!--
When the port and scheme are omitted, the HTTP request's port and scheme are used.
If these are wrong because of virtualization, they can be explicitly set here to
ensure proper redirect generation.
-->
<!--
<Site id="42" name="virtual.example.org" scheme="https" port="443"/>
-->
</ISAPI>
Host name corrisponde sempre all'host FQDN; con path si indica la location da proteggere mediante shibboleth (in questo esempio la location protetta è /secure)
<RequestMapper type="Native">
<RequestMap>
<!--
The example requires a session for documents in /secure on the containing host with http and
https on the default ports. Note that the name and port in the <Host> elements MUST match
Apache's ServerName and Port directives or the IIS Site name in the <ISAPI> element above.
-->
<Host name="app-infocad-dev2016.unipr.it">
<Path name="secure" authType="shibboleth" requireSession="true"/>
</Host>
<!-- Example of a second vhost mapped to a different applicationId. -->
<!--
<Host name="admin.example.org" applicationId="admin" authType="shibboleth" requireSession="true"/>
-->
</RequestMap>
</RequestMapper>
Configurare l'entityID del proprio shibboleth service provider (è una label, che di norma corrisponde al proprio schema+FQDN+/shibboleth → https://app-infocad-dev2016.unipr.it/shibboleth):
<ApplicationDefaults entityID="https://app-infocad-dev2016.unipr.it/shibboleth"
REMOTE_USER="eppn subject-id pairwise-id persistent-id"
cipherSuites="DEFAULT:!EXP:!LOW:!aNULL:!eNULL:!DES:!IDEA:!SEED:!RC4:!3DES:!kRSA:!SSLv2:!SSLv3:!TLSv1:!TLSv1.1">
<!--
Inoltre configurare opportunamente l'elemento Sessions e valorizzare l'entityID di riferimento per le autenticazioni, in questo caso dell'IdP UNIPR https://shibidp.unipr.it/idp/shibboleth
<Sessions lifetime="28800" timeout="3600" relayState="ss:mem"
checkAddress="true" handlerSSL="true" cookieProps="https">
<!--
Configures SSO for a default IdP. To properly allow for >1 IdP, remove
entityID property and adjust discoveryURL to point to discovery service.
You can also override entityID on /Login query string, or in RequestMap/htaccess.
-->
<SSO entityID="https://shibidp.unipr.it/idp/shibboleth">
SAML2
</SSO>
Configurare il MetadataProvider (in questo caso staticamente via file)
<!-- Example of locally maintained metadata. -->
<MetadataProvider type="XML" validate="true" path="partner-metadata.xml"/>
In questo caso nel file partner-metadata.xml andrà salvato il metadata IdP UNIPR scaricabile dal link https://shibidp.unipr.it/idp/shibboleth
attribute-map.xml
Includere gli elementi Attributi necessari e richiesti durante la fase di accreditamento, come da istruzioni presenti al seguenti link Service Provider: HowTo Shibboleth
Esempio:
<Attribute name="urn:oid:2.5.4.3" id="cn"/>
<Attribute name="urn:oid:2.5.4.4" id="sn"/>
<Attribute name="urn:oid:2.5.4.42" id="givenName"/>
<Attribute name="urn:oid:2.16.840.1.113730.3.1.241" id="displayName"/>
<Attribute name="urn:oid:0.9.2342.19200300.100.1.1" id="uid"/>
<Attribute name="urn:oid:0.9.2342.19200300.100.1.3" id="mail"/>
Generare i certificati per la firma e la crittografia delle asserzioni
I ceritifcati generati localmente per mezzo del tool “seckeygen.bat” presente in C:\opt\shibboleth-sp\etc\shibboleth, servono esclusivamente per la firma e la crittografia delle asserzioni e dopo la generazione saranno presenti in linea nel metadata del service provider, che dovrà successivamente essere scaricato ed inviato all'IdP UNIPR come da istruzioni presenti qui Service Provider: HowTo Shibboleth
C:\opt\shibboleth-sp\etc\shibboleth>keygen.bat --help usage: keygen [-h hostname for cert] [-y years to issue cert] [-e entityID to embed in cert] [-n filename prefix] [-o output dir]
Esempio:
keygen.bat -h app-infocad-dev2016.unipr.it -y 10 -e https://app-infocad-dev2016.unipr.it/shibboleth -n sp-signing -INVIO- keygen.bat -h app-infocad-dev2016.unipr.it -y 10 -e https://app-infocad-dev2016.unipr.it/shibboleth -n sp-encrypt -INVIO-
In questo modo si generano due certificati rispettivamente dedicati per la firma e per la crittografia.
Questi saranno referenziati nel file shibboleth2.xml nella sezione
<!-- Simple file-based resolvers for separate signing/encryption keys. -->
<CredentialResolver type="File" use="signing"
key="sp-signing-key.pem" certificate="sp-signing-cert.pem"/>
<CredentialResolver type="File" use="encryption"
key="sp-encrypt-key.pem" certificate="sp-encrypt-cert.pem"/>
</ApplicationDefaults>
Scaricare il proprio Metadata da inviare a UNIPR
E' possibile scaricare una versione del Metadata relativo al proprio SP direttamente dal link:
https://app-infocad-dev2016.unipr.it/Shibboleth.sso/Metadata
Esempio di Metadata generato:
<!--
This is example metadata only. Do *NOT* supply it as is without review,
and do *NOT* provide it in real time to your partners.
-->
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" ID="_ead11ca66483ec6b1d726d99486e48af73d37f6a" entityID="https://app-infocad-dev2016.unipr.it/shibboleth">
<md:Extensions xmlns:alg="urn:oasis:names:tc:SAML:metadata:algsupport">
<alg:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha512"/>
<alg:DigestMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#sha384"/>
<alg:DigestMethod Algorithm="http://www.w3.org/2001/04/xmlenc#sha256"/>
<alg:DigestMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#sha224"/>
<alg:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#ecdsa-sha512"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#ecdsa-sha384"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#ecdsa-sha256"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#ecdsa-sha224"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha512"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha384"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#rsa-sha256"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2009/xmldsig11#dsa-sha256"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2001/04/xmldsig-more#ecdsa-sha1"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
<alg:SigningMethod Algorithm="http://www.w3.org/2000/09/xmldsig#dsa-sha1"/>
</md:Extensions>
<md:SPSSODescriptor protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:Extensions>
<init:RequestInitiator xmlns:init="urn:oasis:names:tc:SAML:profiles:SSO:request-init" Binding="urn:oasis:names:tc:SAML:profiles:SSO:request-init" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/Login"/>
</md:Extensions>
<md:KeyDescriptor use="signing">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:KeyName>app-infocad-dev2016.unipr.it</ds:KeyName>
<ds:KeyName>https://app-infocad-dev2016.unipr.it/shibboleth</ds:KeyName>
<ds:X509Data>
<ds:X509SubjectName>CN=app-infocad-dev2016.unipr.it</ds:X509SubjectName>
<ds:X509Certificate>MIIEVzCCAr+gAwIBAgIUdAlLy/PFQKS2nz24qba2jJl7zDQwDQYJKoZIhvcNAQEL
BQAwJzElMCMGA1UEAxMcYXBwLWluZm9jYWQtZGV2MjAxNi51bmlwci5pdDAeFw0y
MjAyMTcwODU5MzdaFw0yMzAyMTcwODU5MzdaMCcxJTAjBgNVBAMTHGFwcC1pbmZv
Y2FkLWRldjIwMTYudW5pcHIuaXQwggGiMA0GCSqGSIb3DQEBAQUAA4IBjwAwggGK
AoIBgQC56e/5MdgstUlAxAYKZusASX3k5lWwUe4ChMHnbSJI4SwO3sYi4vT7ip7B
hYkUALbvSWJz+ALa5vrQh7kcc5rryeryrtyetytyAlxQyp/FrUJAL7FDaBylFiI9
rt7SF2istpwIClwyh/jGiNwhRH2QY/YbPz4S/3oNJI0PGb9WcfjIZQk/INRe40EJ
VlZcEE7PGOGiYqaMuKb+ON03dKWJkPfe3INBA19P8s+tCLdMzoyY03LwFoCRAZ2y
Ah7OVBWZT9o97Bd1r++Shv4u1YSYNOKaQNjq6FmBC52C7p6c0ynEUIsEAXrtxQCF
RIfHmGnMICBLkzhH0++ZyYqcf8v5auMY2s/O9PgrXBVj5hTTAT8a+ofRcBdRWEnz
bqG4yjGDV7PsstZb7WSJqYICNlYnQ+zVPgHUC37onp+JW/vhBbK/5TATPnkJDl+x
pFT33DsCAwEAAaN7MHkwWAYDVR0RBFEwT4IcYXBwLWluZm9jYWQtZGV2MjAxNi51
bmlwci5pdIYvaHR0cHM6Ly9hcHAtaW5mb2NhZC1kZXYyMDE2LnVuaXByLml0L3No
aWJib2xldGgwHQYDVR0OBBYEFJPioiVDyRcwWRKvGmDep5JSBZxVMA0GCSqGSIb3
DQEBCwUAA4IBgQCvOPZqy45+vf1IYDP7i7Yl+WXq6EyY7PTum7rdmHqzALaEjcKZ
zBjrnj1V4D/CKnU4Q27GC7+ugenk6SLmOsUV5RAlNf0eZ5eX+Vh2e7jgBKXgzoMj
wICOJk5eMXH3MfIPCh63QDh+zLU4iIJhqQw/9xdzinlqh3y7h/mrh/i4k+mGD77Z
pJAKWNxcEdaj99LRUTgkwFP9Prtyr4y465rOXVC502UVBzc8XwH4XtWtWaFRPqQU
NP7Wvy2XHxcKwGQbYPJfRBf4pmgoJe5NGIUlWnT1pL+1rE4hbo2iwz2w8dAPCjAv
79w4K1+VL8bDLqzhQCXr6LFTS8AEc+QOSWAuidCIKfR0VQcIL8GfK65gu2gdhJ66
RKB6dAMIgj56Da7pGk2Z3tKsuDfOqeOtmK4fE+xMo3RyOU7bWm7wEyM0Y95s9B7N
26V6oUNYusWZC0UH0UYN1wh6oXShfYwD4291vIgjN3Om3UMe92WFeeEKd4JyxGt7
GialwGVCPjQpvZs=
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</md:KeyDescriptor>
<md:KeyDescriptor use="encryption">
<ds:KeyInfo xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:KeyName>app-infocad-dev2016.unipr.it</ds:KeyName>
<ds:KeyName>https://app-infocad-dev2016.unipr.it/shibboleth</ds:KeyName>
<ds:X509Data>
<ds:X509SubjectName>CN=app-infocad-dev2016.unipr.it</ds:X509SubjectName>
<ds:X509Certificate>MIIEVzCCAr+gAwIBAgIUGP+/MVob2czUBSHCg7per+pOnJMwDQYJKoZIhvcNAQEL
BQAwJzElMCMGA1UEAxMcYXBwLWluZm9jYWQtZGV2MjAxNi51bmlwci5pdDAeFw0y
MjAyMTcwODU5NTFaFw0yMzAyMTcwODU5NTFaMCcxJTAjBgNVBAMTHGFwcC1pbmZv
Y2FkLWRldjIwMTYudW5pcHIuaXQwggGiMA0GCSqGSIb3DQEBAQUAA4IBjwAwggGK
AoIBgQDMusBGKj4LGUwdhurF7dFPwVKknEzYp9xTouWfIOkLynPnUOwbeouQgk1G
imaDK74Op3mE9TgZyDB4sSV0ynXkPLelNOr5DDWtG9WQBZvJJQ7DQ7yq7ogymMPs
LAKACVGmusNpBmn0BSVpT56MPKrXfpyG7L7HrgI6TzQ+FohFsFH0t+kGjAtxPZkf
99ORyodFPNLZrthrththtrhy2KabqcfgE5rbpsss8arH0WdlRv+s4tWGhp+mK2pH
Ebz99Pkq3tWcSPXDZB/RGtWBrTnnZksZc4MGJMeAf691sCA/kzoDZNiuGrnKa27H
CpxruR+c9+58XAfWuKaBkg0/IQC+yIMCR3Q7W9ICx7g4w7KksGPYPmxHIAMmIgPC
V4/ZSluIPOkdSdzFyaUqzRuWMk/BhxSeBvfN/APubSjzVMpMo+dn5Vqp6oynEQkd
77UsI1hzPURhlVX6ir5kqyDMB5fK2iO5PjSmf0E2sRXlrvat/2YkwRV7KnD7PaZG
X21vV/MCAwEAAaN7MHkwWAYDVR0RBFEwT4IcYXBwLWluZm9jYWQtZGV2MjAxNi51
bmlwci5pdtygrewtghrthcHAtaW5mb2NhZC1kZXYyMDE2LnVuaXByLml0L3No343
aWJib2xldGgwHQYDVR0OBBYEFDiTah7AYoXJMT6e49+eTzwJaOT/MA0GCSqGSIb3
DQEBCwUAA4IBgQB5isu/8YU9e1vKBntbE8Zyy6nmXqxfqKJ8c6isVsqnsJNP/teM
W/51Huz5B8XyE2bxZpiVua4Fh5pXCqh1xzV04TTGy8YZL83VgZN5ZFhAGEVzpWo9
3MupMhl1BRC8aBNmvxg36iq7rVopISGLeY8PwF+/2k6jZUU6BCpjwvIqbH18uMZZ
8Fe3D1siu8D/dBeWVjx258kwHcsBERpwl8l1DPl/9xFgAOCe95CYakrHSHjO8M+3
uYwewymWEKG9eGozrHyA7YbL4VeEnUJBWxEf7H+al5cvfh5ZB4XzJc5OM3R5jWc9
kubznp/9sCNkGjEzO3BSXFquD+HF8ZMg7VVBiLcfwgNi6VndSufpSnkckyp2OZkA
WTRBLCT+EvKQw+IuOB8+EeTYPezkVY0j8u8xIla6GxdmmY4E21eiDK/4AvxofKob
wY8SmNEiNNQ/U1VOfAU1mfeENLAVWaFvUBJ7wsgXcwygOcCF9bmRyGmZQwJPeKU8
KIqyoFclQ8sAXWU=
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
<md:EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes128-gcm"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes192-gcm"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#aes256-gcm"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes128-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes192-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#tripledes-cbc"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2009/xmlenc11#rsa-oaep"/>
<md:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p"/>
</md:KeyDescriptor>
<md:ArtifactResolutionService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/Artifact/SOAP" index="1"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:SOAP" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/SLO/SOAP"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/SLO/Redirect"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/SLO/POST"/>
<md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/SLO/Artifact"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/SAML2/POST" index="1"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST-SimpleSign" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/SAML2/POST-SimpleSign" index="2"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Artifact" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/SAML2/Artifact" index="3"/>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:PAOS" Location="https://app-infocad-dev2016.unipr.it/Shibboleth.sso/SAML2/ECP" index="4"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>