Questa è una vecchia versione del documento!
Indice
Passi per configurare Shibboleth service provider su Windows Server + IIS
- Sistema operativo: Windows Server 2016
- Versione IIS: 10.0.14393.0
- Versione shibboleth SP: 3.0.4.2
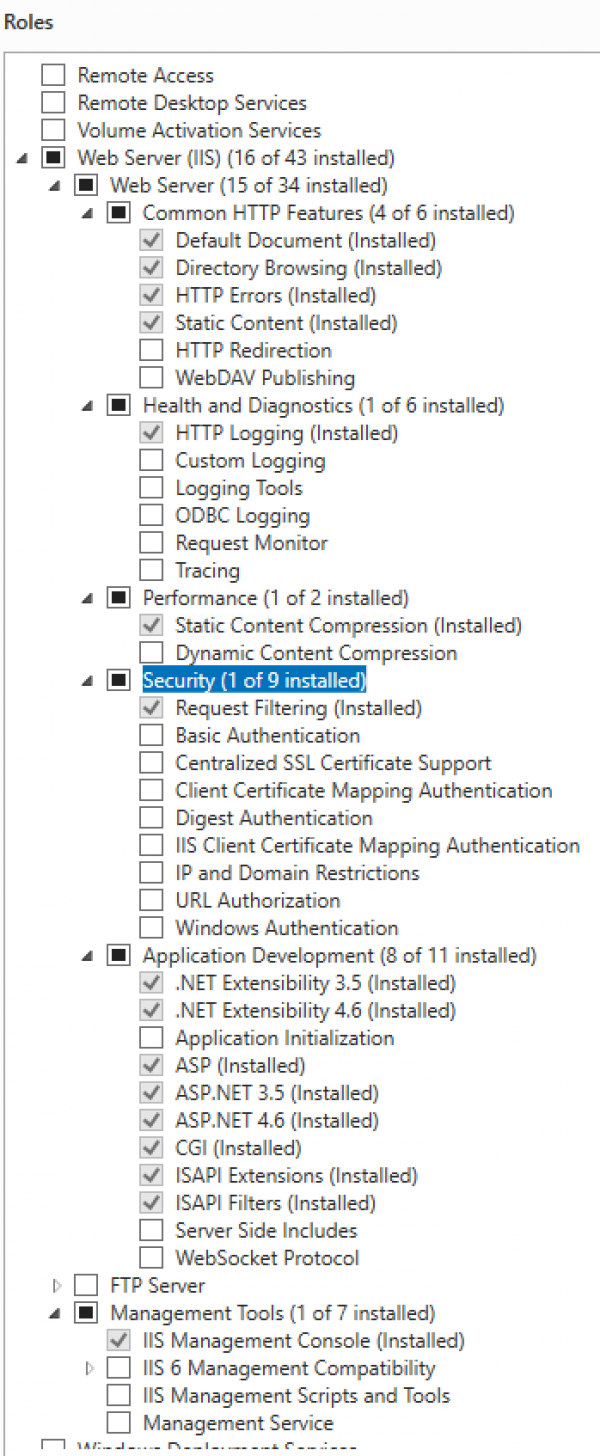
Ruoli e funzioni Windows Server
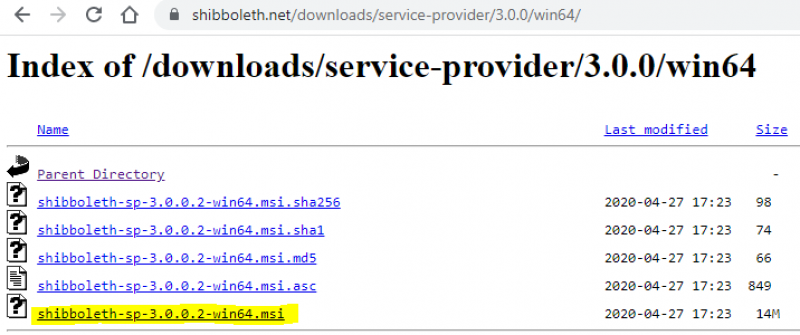
Download Shibboleth service provider
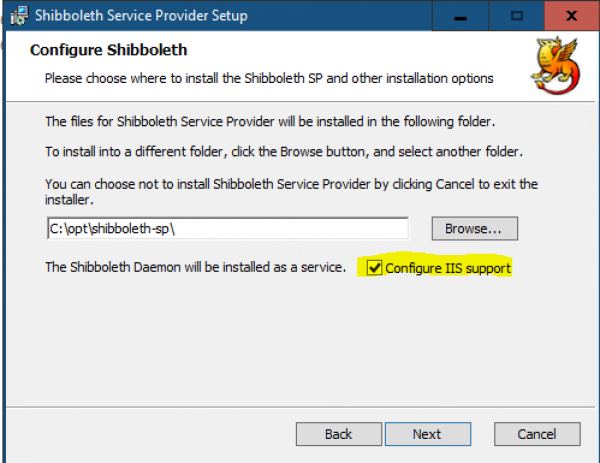
Installazione Shibboleth service provider
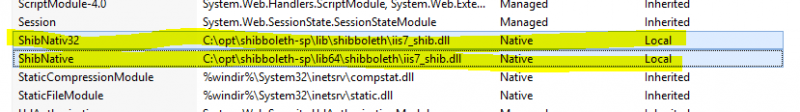
Verificare la corretta installazione delle DLL in IIS
Verificare che nel Site opportuno, nella sezione “Modules” abbia le i moduli nativi Shibboleth (32/64 bit)
Configurazione shibboleth service provider
(cambiare cartella in C:\opt\shibboleth-sp\etc\shibboleth)
shibboleth2.xml
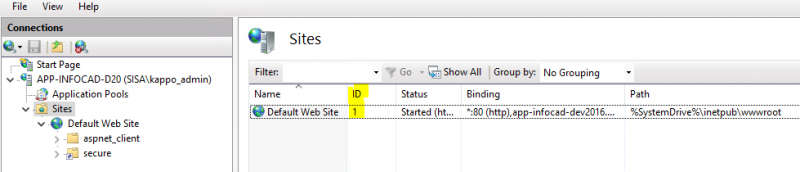
(Sezioni da personalizzare) Site id deve corrpispondere all'ID presente in IIS; il Site name corrisponde all'host (FQDN)
<ISAPI normalizeRequest="true" safeHeaderNames="true">
<!--
Maps IIS Instance ID values to the host scheme/name/port. The name is
required so that the proper <Host> in the request map above is found without
having to cover every possible DNS/IP combination the user might enter.
-->
<Site id="1" name="app-infocad-dev2016.unipr.it"/>
<!--
When the port and scheme are omitted, the HTTP request's port and scheme are used.
If these are wrong because of virtualization, they can be explicitly set here to
ensure proper redirect generation.
-->
<!--
<Site id="42" name="virtual.example.org" scheme="https" port="443"/>
-->
</ISAPI>
Host name corrisponde sempre all'host FQDN; con path si indica la location da proteggere mediante shibboleth (in questo esempio la location protetta è /secure)
<RequestMapper type="Native">
<RequestMap>
<!--
The example requires a session for documents in /secure on the containing host with http and
https on the default ports. Note that the name and port in the <Host> elements MUST match
Apache's ServerName and Port directives or the IIS Site name in the <ISAPI> element above.
-->
<Host name="app-infocad-dev2016.unipr.it">
<Path name="secure" authType="shibboleth" requireSession="true"/>
</Host>
<!-- Example of a second vhost mapped to a different applicationId. -->
<!--
<Host name="admin.example.org" applicationId="admin" authType="shibboleth" requireSession="true"/>
-->
</RequestMap>
</RequestMapper>
Configurare l'entityID del proprio shibboleth service provider (è una label, che di norma corrisponde al proprio schema+FQDN+/shibboleth → https://app-infocad-dev2016.unipr.it/shibboleth):
<ApplicationDefaults entityID="https://app-infocad-dev2016.unipr.it/shibboleth"
REMOTE_USER="eppn subject-id pairwise-id persistent-id"
cipherSuites="DEFAULT:!EXP:!LOW:!aNULL:!eNULL:!DES:!IDEA:!SEED:!RC4:!3DES:!kRSA:!SSLv2:!SSLv3:!TLSv1:!TLSv1.1">
<!--
Inoltre configurare opportunamente l'elemento Sessions e valorizzare l'entityID di riferimento per le autenticazioni, in questo caso dell'IdP UNIPR https://shibidp.unipr.it/idp/shibboleth
<Sessions lifetime="28800" timeout="3600" relayState="ss:mem"
checkAddress="true" handlerSSL="true" cookieProps="https">
<!--
Configures SSO for a default IdP. To properly allow for >1 IdP, remove
entityID property and adjust discoveryURL to point to discovery service.
You can also override entityID on /Login query string, or in RequestMap/htaccess.
-->
<SSO entityID="https://shibidp.unipr.it/idp/shibboleth">
SAML2
</SSO>